Advanced MikroTik RouterOS Firewall Custom Rules And Filters
As a farmer, network security may not be the first thing on your mind. However, it is crucial to ensure that your network is protected from potential threats and attacks. One tool that you can use to achieve this is a firewall, and in this article, we will go over the basics of configuring a Mikrotik Router OS firewall.
![Firewall Podstawy [konfiguracja Mikrotik Router OS] - NetAdminPro](https:\/\/netadminpro.pl\/wp-content\/uploads\/2022\/09\/Mikrotik-RouterOS-Firewall-Tworzenie-Nowej-Reguly-1536x928.png)
What is a firewall?
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. In essence, it acts as a barrier between your network and the rest of the internet, allowing only authorized traffic to pass through.
Why is a firewall important?
A firewall is important because it provides an extra layer of security between your network and potential threats from the internet. By blocking unauthorized access attempts and filtering out malicious traffic, a firewall can help prevent your network from being compromised.
Configuring a Mikrotik Router OS Firewall
Now that we understand the importance of a firewall, let's dive into how to configure one using Mikrotik Router OS.
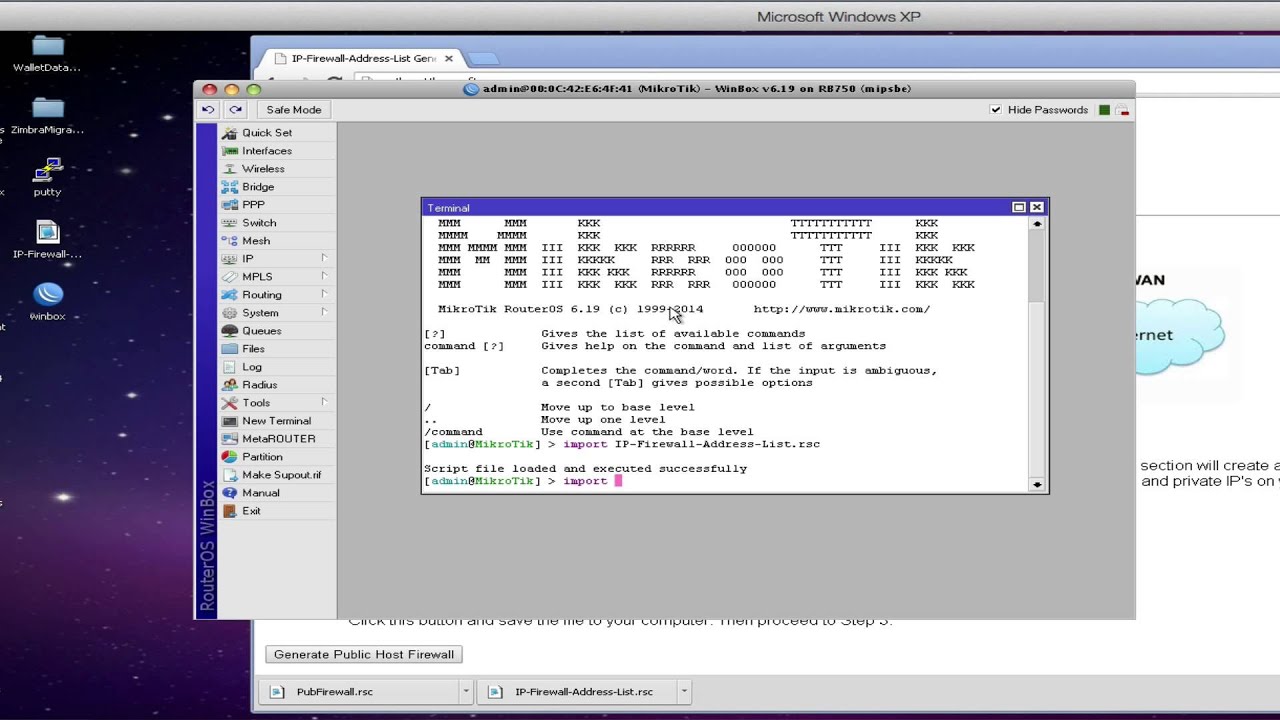
Step 1: Access the RouterOS Firewall Configuration
The first step is to access the Mikrotik Router OS firewall configuration. To do this, log in to your Mikrotik Router OS using the Winbox configuration tool. Once you are logged in, go to the "IP" menu and select "Firewall".
Step 2: Add a New Firewall Rule
Once you are in the Firewall configuration menu, click the "Filter Rules" tab. Then, click the "Add New" button to create a new firewall rule. This will bring up the "New Firewall Rule" window.
Step 3: Configure the Firewall Rule
Now, it's time to configure the firewall rule. There are several fields that you will need to fill out in order to set up your firewall rule:
- Chain: This field determines how the rule will be applied. In most cases, you will want to leave this set to "input" or "forward", depending on your needs.
- Action: This field determines what happens to the traffic that matches the rule. You can choose to allow the traffic, drop it, or reject it. In most cases, you will want to choose "drop" or "reject" for traffic that fails to meet the criteria of your rule.
- Protocol: This field specifies the protocol that the firewall rule will apply to. You can choose from a variety of protocols, including TCP, UDP, ICMP, and others.
- Src. Address: This field specifies the source address of the traffic that the firewall rule will apply to. You can enter individual IP addresses or IP ranges here.
- Dst. Address: This field specifies the destination address of the traffic that the firewall rule will apply to. You can enter individual IP addresses or IP ranges here.
- Src. Port: This field specifies the source port of the traffic that the firewall rule will apply to. You can enter individual port numbers or port ranges here.
- Dst. Port: This field specifies the destination port of the traffic that the firewall rule will apply to. You can enter individual port numbers or port ranges here.
- Comment: This field allows you to add a comment or description to your firewall rule for future reference.
Once you have filled out all of the necessary fields, click "OK" to save your new firewall rule.
Step 4: Apply the Firewall Rule
After you have created your new firewall rule, it's time to apply it to your network. To do this, go to the "Filter Rules" tab in the Firewall configuration menu and find the rule that you just created. Then, select the checkbox next to the rule and click the "Enable" button.
Step 5: Test Your Firewall Rule
After you have applied your firewall rule, it's important to test it to ensure that it is working as expected. You can test your firewall rule by attempting to access a resource that should be blocked by the rule. For example, if you created a rule to block traffic from a specific IP address, try accessing a resource from that IP address to see if the rule is working.
Conclusion
In conclusion, configuring a firewall is an essential step in ensuring the security of your network. By using Mikrotik Router OS to create a firewall rule, you can help prevent unauthorized access and protect your network from potential threats. Remember to test your firewall rule to ensure that it is functioning properly and stay vigilant for any potential security risks.



Post a Comment for "Advanced MikroTik RouterOS Firewall Custom Rules And Filters"