Transparent Proxy Configuration On MikroTik RouterOS
Wow, have you ever heard of transparent proxying? If not, let us fill you in on this amazing technique that can help protect your network from malicious activity.
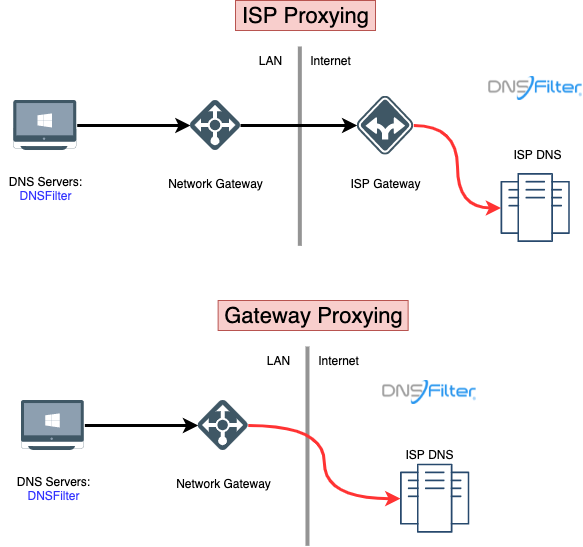
Transparent proxying is a technique used to redirect network traffic through a proxy server without the knowledge or consent of the end user. The end user's requests are intercepted and sent to the proxy server, which then sends the request to the original destination. The response from the original destination is sent back to the proxy server, which then forwards the response to the end user.
Why would you want to use transparent proxying? There are several reasons:
- Increased security: By redirecting traffic through a proxy server, you can prevent malicious activity from reaching your network. The proxy server can filter out known threats and block them before they reach your network.
- Better performance: Proxy servers can cache frequently requested content, which can improve network performance and reduce latency.
- Content filtering: Transparent proxying can be used to enforce content filtering policies on your network. This can prevent users from accessing inappropriate content and protect your organization from liability.
How does transparent proxying work? There are several components:
- Proxy server: This is the server that intercepts the end user's requests and sends them to the original destination.
- Client: This is the device that the end user is using to access the network. It could be a computer, mobile device, or other internet-connected device.
- Destination: This is the server that the end user is requesting content from. It could be a website, application, or other service.
When transparent proxying is used, the client does not know that their requests are being intercepted and sent through a proxy server. The proxy server appears to the client as the destination server, and the destination server appears to the proxy server as the client.
There are several types of transparent proxying:
- HTTP proxy: This type of proxy is used for HTTP traffic only. It is the most common type of proxy.
- HTTPS proxy: This type of proxy is used for secure HTTPS traffic. It can be more difficult to set up than an HTTP proxy.
- SOCKS proxy: This type of proxy can be used for any type of traffic, including TCP and UDP traffic.
Transparent proxying can be set up in several ways:
- Transparent proxy: This type of proxy is set up so that the client does not need to make any configuration changes to their device. All traffic is automatically intercepted and sent through the proxy server.
- Explicit proxy: This type of proxy requires the client to configure their device to use the proxy server. This can be done through the device's network settings.
So, what are the benefits of using transparent proxying? Here are a few:
- Improved security: By redirecting traffic through a proxy server, you can prevent malicious activity from reaching your network. The proxy server can filter out known threats and block them before they reach your network.
- Better performance: Proxy servers can cache frequently requested content, which can improve network performance and reduce latency.
- Content filtering: Transparent proxying can be used to enforce content filtering policies on your network. This can prevent users from accessing inappropriate content and protect your organization from liability.
- Reduced bandwidth usage: By caching frequently requested content, you can reduce the amount of bandwidth used by your network.
- Improved user experience: By reducing latency and improving network performance, you can improve the overall user experience for your employees or customers.
- Easy to set up: Transparent proxying can be set up and configured quickly and easily, with no need for end users to make any configuration changes to their devices.
Overall, transparent proxying is a powerful technique that can help protect your network from malicious activity and improve network performance. If you're interested in setting up transparent proxying on your network, be sure to consult with a knowledgeable IT professional to ensure that it is set up correctly.



Post a Comment for "Transparent Proxy Configuration On MikroTik RouterOS"