Secure Remote Access With MikroTik VPN Solutions
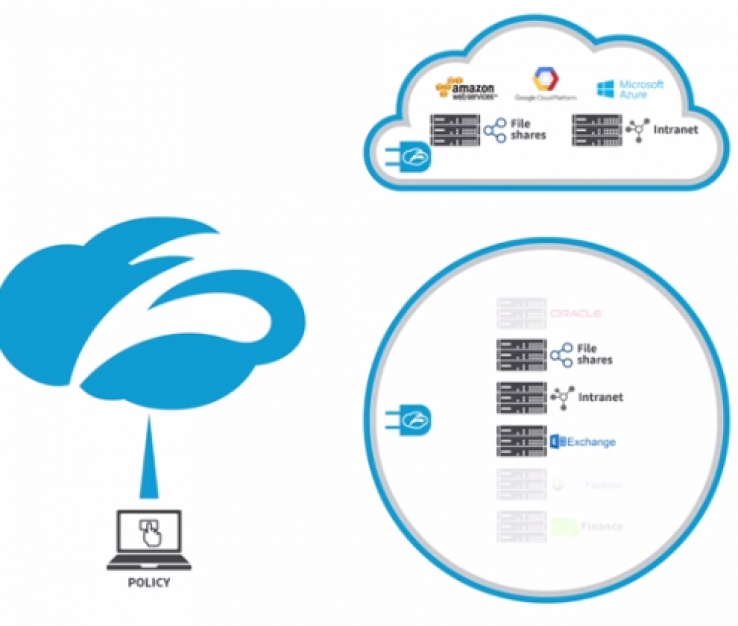
In today's fast-paced digital world, remote access has become a must-have for businesses of all sizes. However, remote access can also be a significant source of cybersecurity risks, which is why many companies have relied on virtual private networks (VPNs) to keep their networks secure. Unfortunately, VPNs are slow, complicated, and can be challenging to configure, making remote access a dreaded process for many employees.
But what if there was a way to provide secure remote access without VPNs? Enter zero-trust network access (ZTNA).
Details
ZTNA is a security framework that provides access to specific applications or services based on the user's identity and contextual information. Unlike traditional network security models, where users are granted unrestricted access once inside a secured perimeter, ZTNA provides the least privileged access possible to users, devices, and applications.
One of the key benefits of ZTNA is its ability to reduce attack surfaces. In a traditional security model, once a user gains access to the network, they can move laterally and gain access to other resources. In contrast, ZTNA allows users to access only the specific application or service they need, reducing the potential for lateral movement.
ZTNA also simplifies the process of granting access to applications. Instead of setting up VPNs or opening ports, IT administrators can use ZTNA to grant role-based access to users based on their identity and business need. This approach streamlines the process of onboarding new employees or contractors and reduces the risk that former employees retain access to company applications and data.
Tips
Implementing ZTNA can seem daunting, but there are several steps that businesses can take to make the process more manageable:
- Perform a comprehensive audit of your existing remote access practices to identify areas of improvement
- Identify the applications and services that require remote access and categorize them based on business value and risk level
- Develop a comprehensive authentication protocol that includes multi-factor authentication (MFA)
- Ensure that all network traffic is encrypted using Transport Layer Security (TLS) or Secure Real-time Transport Protocol (SRTP)
- Consider using micro-segmentation to further reduce attack surfaces and simplify compliance
FAQ
What are the primary benefits of ZTNA?
The primary advantages of ZTNA are improved security and user experience. ZTNA reduces the potential attack surface by providing the least privileged access possible, and it simplifies the process of granting access to remote applications and services, reducing the burden on IT administrators and employees.
What is the difference between ZTNA and VPNs?
ZTNA and VPNs both provide remote access to company resources, but ZTNA does so using a zero-trust security model, while VPNs use a perimeter-based security model. ZTNA provides the least privileged access possible based on the user's identity and contextual information, while VPNs grant access to the entire network once inside the perimeter.
Is ZTNA difficult to implement?
Implementing ZTNA can be challenging, but it doesn't have to be. With the right planning and resources, businesses can transition to a ZTNA model over time, starting with critical applications and services and expanding as needed. IT administrators should work closely with business units to develop a comprehensive authentication protocol and identify the applications and services that require remote access.
Can ZTNA help with regulatory compliance?
ZTNA can help businesses comply with a variety of regulatory requirements, including PCI DSS and HIPAA, by providing a comprehensive audit trail of all remote access activity and ensuring that only authorized users have access to sensitive data.
What are some of the challenges of implementing ZTNA?
One of the primary challenges of implementing ZTNA is managing the user experience. Because ZTNA grants access based on the user's identity and contextual information, there is a risk that legitimate users will be denied access to critical applications and services. IT administrators must work closely with business units to ensure that the authentication process is streamlined and user-friendly.
Secure remote access is a critical part of doing business in today's digital world. If you're looking for a more secure, streamlined solution than traditional VPNs, zero-trust network access may be right for your company. By implementing a comprehensive authentication protocol and streamlining the access process, you can reduce the potential for data breaches and improve the user experience for your employees.




Post a Comment for "Secure Remote Access With MikroTik VPN Solutions"