Exploring MikroTik Router Traffic Flow Analysis
Have you ever wondered how MikroTik firewall actually works? Well, let me tell you, it's not rocket science. In fact, it's so simple that even a cat could probably figure it out (okay, maybe not a cat, but you get the idea).
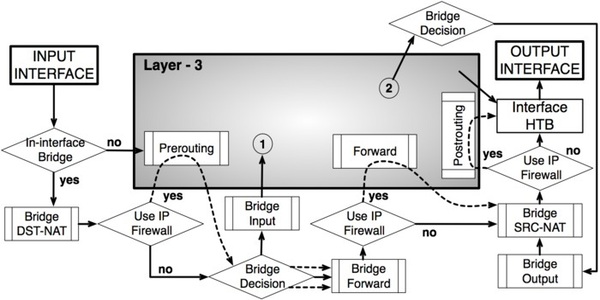
Before we dive into the nitty-gritty details, let's first take a look at a basic concept of MikroTik firewall. Essentially, a firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. In other words, it acts as a barrier between your computer network and the outside world, protecting you from unauthorized access, viruses, and other malicious attacks.
Now that we've got that out of the way, let's take a closer look at how MikroTik firewall actually works. Here are the key points:
1. Packet Filtering
The first and most basic level of firewall security is packet filtering. This involves analyzing each individual data packet that enters or exits your network and applying predefined security rules to determine whether it should be allowed or blocked.
For example, you could set a rule that blocks all incoming data packets from a particular IP address or port, or only allows incoming traffic that meets certain criteria (such as a specific protocol or application).
2. NAT (Network Address Translation)
NAT is another important aspect of MikroTik firewall security. It allows your network to use a private IP address range (such as 192.168.x.x) to communicate with the outside world through a single public IP address (provided by your ISP).
By using NAT, you can hide the internal IP addresses of your computers and devices from the outside world, making it more difficult for hackers to penetrate your network.
3. Connection Tracking
Connection tracking is a technique used by MikroTik firewall to keep track of all incoming and outgoing network connections. It allows the firewall to detect and prevent malicious attacks by monitoring the state of each connection and comparing it to predefined security rules.
For example, if the firewall detects an unusually high number of connections from a particular IP address or port, it can automatically block all further connections from that source in order to prevent a potential attack.
4. Layer 7 Protocol Analysis
Layer 7 protocol analysis is a more advanced form of security that involves analyzing the content of each data packet to determine the specific type of traffic (such as HTTP, FTP, or SMTP).
By analyzing the content of each packet at a deeper level, MikroTik firewall can better protect your network from more complex attacks that may attempt to bypass traditional packet filtering or NAT security measures.
5. VPN and Tunneling
MikroTik firewall also supports VPN and tunneling technologies, which allow you to create secure and encrypted connections between remote networks or devices.
With VPN and tunneling, you can use the Internet to securely connect two or more remote networks as if they were part of the same physical network. This can be especially useful for businesses or organizations with multiple locations that need to securely communicate with each other.
So, there you have it - a basic overview of how MikroTik firewall works. Now, while we may have been joking around a bit at the beginning of this post, it's worth remembering that network security is no laughing matter. Whether you're a home user or a business owner, having a reliable and effective firewall is essential for keeping your network safe and secure.




Post a Comment for "Exploring MikroTik Router Traffic Flow Analysis"