VPN Protocols Demystified Choosing The Right Encryption For Your MikroTik Router
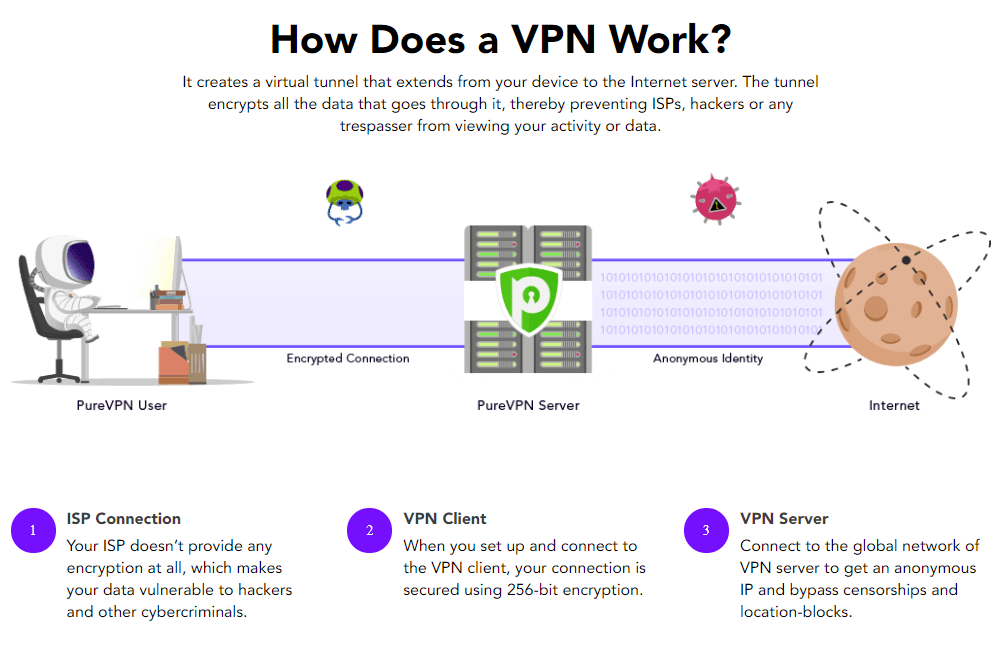
Are you wondering what VPN protocols are and which one you should use? Look no further. In this article, we will cover all the important information about VPN protocols, so you can make an informed decision.
What are VPN protocols?
VPN protocols are the set of instructions that determine how data is transmitted through a VPN connection. The most popular VPN protocols are:
- OpenVPN
- IPSec/L2TP
- PPTP
- SSTP
- IKEv2

Which VPN protocol should I use?
The VPN protocol you should use depends on your needs and priorities. Here's a quick rundown of the advantages and disadvantages of each protocol.
OpenVPN
OpenVPN is arguably the most popular VPN protocol because it's open-source, secure, and versatile. It's compatible with most operating systems and devices and supports advanced encryption algorithms, making it an excellent choice for online security.
The main downside of OpenVPN is that it can be slower than other protocols due to its advanced encryption, which can be a problem for streaming and gaming.
IPSec/L2TP
IPSec/L2TP is a combined protocol that combines the security of IPSec with the speed of L2TP. It's a common choice for businesses and organizations because it's highly secure and can handle high traffic loads.
The downside of this protocol is that it can be difficult to set up and configure, and it can be slow due to the double encryption.
PPTP
PPTP is an old and outdated protocol that's rarely used today. It's fast and easy to set up, but it's also highly insecure and can be easily compromised by hackers.
Unless you're absolutely sure that PPTP is the only option available to you, we recommend avoiding it altogether.
SSTP
SSTP is a protocol developed by Microsoft that's built into Windows operating systems. It's secure and reliable, but it's not as widely supported as other protocols, so it may not be the best choice if you need to connect to a VPN from multiple devices.
IKEv2
IKEv2 is a fast and secure protocol that's ideal for mobile devices. It can handle changes in network connectivity without dropping the VPN connection, making it an excellent choice for people who frequently switch between Wi-Fi and cellular networks.
Details
VPN protocols use different methods to encrypt and transmit your data, which can affect their performance, security, and reliability. Here are some of the technical details you should know:
Encryption
Encryption is the process of encoding your data so that it can't be intercepted or read by anyone else. VPN protocols use different encryption algorithms, such as AES, Blowfish, and Triple DES, which determine how secure and fast the connection is.
Authentication
Authentication is the process of verifying your identity to prevent unauthorized access. VPN protocols use different authentication methods, such as passwords, certificates, and tokens, which determine how secure and easy the connection is.
Tunneling
Tunneling is the process of encapsulating your data in a secure "tunnel" between your device and the VPN server. VPN protocols use different tunneling protocols, such as TCP, UDP, and GRE, which determine how fast and reliable the connection is.
Tips
Here are some tips for choosing the right VPN protocol:
- Choose a protocol that's supported by your device and operating system.
- If you prioritize speed over security, choose a protocol that uses weaker encryption.
- If you prioritize security over speed, choose a protocol that uses strong encryption.
- If you frequently switch between Wi-Fi and cellular networks, choose a protocol that supports mobile devices.
- Avoid outdated and insecure protocols like PPTP.
FAQ
Can I use multiple VPN protocols at the same time?
Technically, yes, but it's not recommended. Using multiple VPN protocols at the same time can slow down your connection and increase the risk of compatibility issues.
Can I switch between VPN protocols?
Yes, most VPN services allow you to switch between different VPN protocols to find the one that works best for you.
Do all VPN services offer the same protocols?
No, VPN services may offer different protocols or variations of the same protocol. It's important to check with your VPN provider to see what protocols are available.
Which VPN protocol is the most secure?
OpenVPN is generally considered the most secure VPN protocol due to its open-source code, robust encryption, and versatile capabilities.
Which VPN protocol is the fastest?
PPTP is generally considered the fastest VPN protocol due to its simplistic design and low encryption overhead. However, we don't recommend using PPTP due to its known vulnerabilities.
Which VPN protocol is the best?
There's no one-size-fits-all answer to this question since the best VPN protocol depends on your individual needs and preferences. We recommend researching each protocol and testing them out to see which one works best for you.

In conclusion, understanding VPN protocols can help you choose the right VPN service that fits your online security, privacy, and performance needs. Assess your priorities, research each protocol, and test them out to find the one that works best for you.
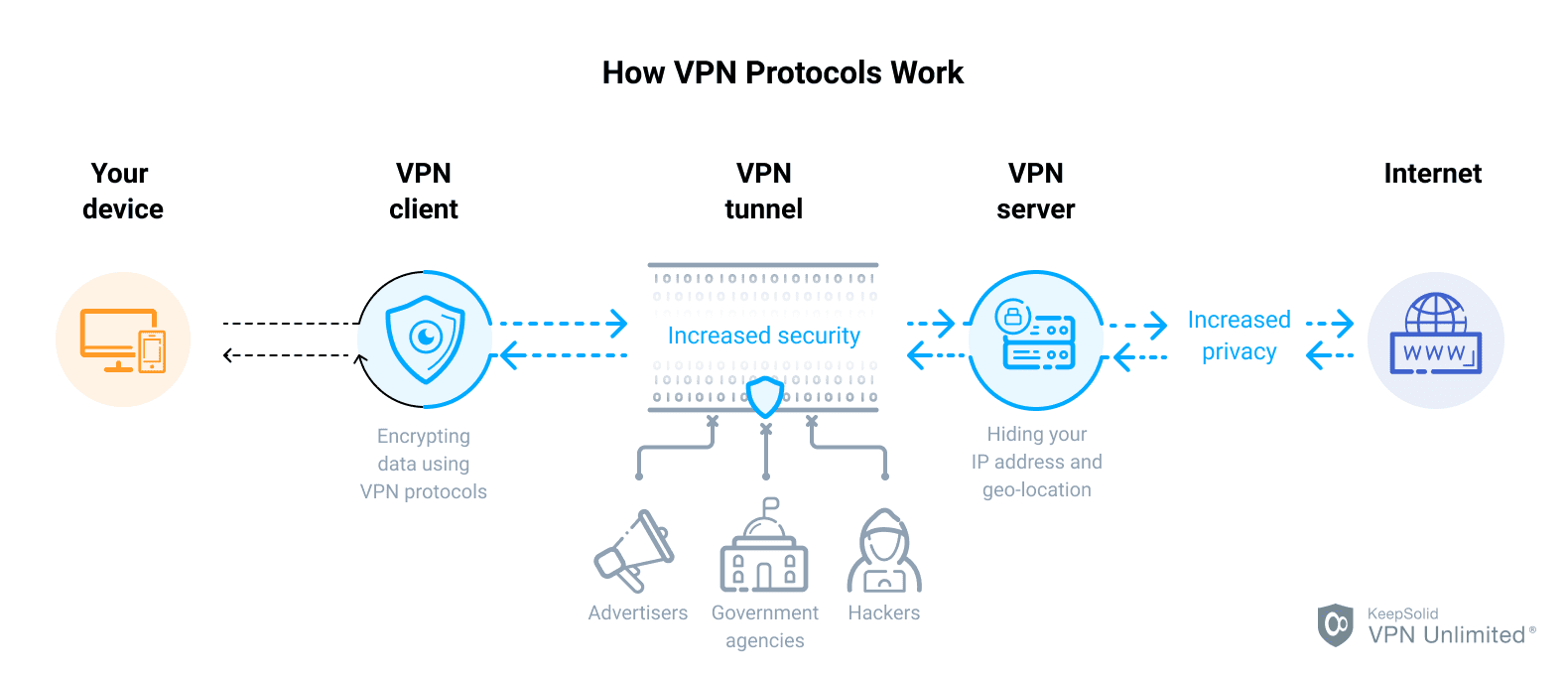


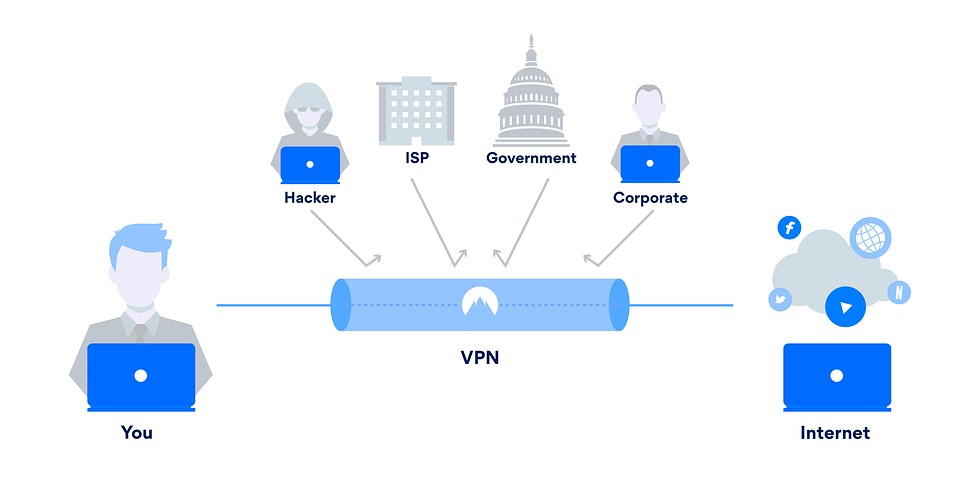
Post a Comment for "VPN Protocols Demystified Choosing The Right Encryption For Your MikroTik Router"