Configuring MikroTik Router Wireless Security Best Practices And Encryption
Securing your Mikrotik router is not optional if you want to protect your network from potential threats. Today, we will discuss the steps you need to take to harden the security of your Mikrotik router and protect your network.

1. Change the default login credentials
The first step towards securing your Mikrotik router is changing the default login credentials. Leaving the default username and password makes it easy for attackers to breach your network. It is important to choose a strong username and password combination. Remember to avoid using common passwords such as '12345' or 'password' as they are easy to guess.
2. Disable unused services
Mikrotik routers come packed with numerous services that may pose a security risk if left enabled. Check for unused services and disable them. VPN and SNMP services should only be enabled if they are in use. This minimizes the attack surface of your router.
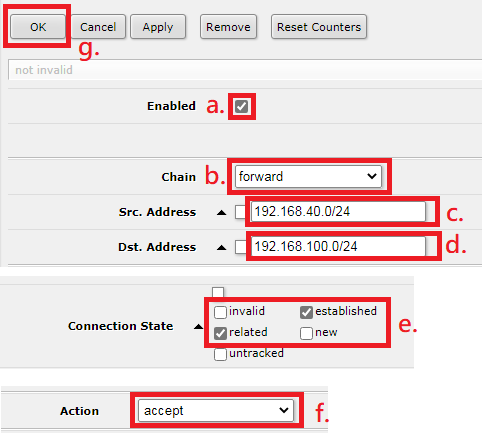
3. Enable firewall rules
Firewall rules help to filter traffic for both inbound and outbound traffic. The firewall prevents unauthorized access and protects against attacks such as Denial of Service (DoS) attacks. Ensure that you have a well-configured firewall that blocks any suspicious traffic.
4. Update your router firmware
Router manufacturers release firmware updates regularly to fix existing vulnerabilities and improve performance. Updating your router firmware to the latest version keeps your router secure and reduces the chances of attackers exploiting known vulnerabilities.
5. Securing administrative access
Limiting administrative access to the router is a crucial step towards maintaining security. Restricting administrative access ensures that only authorized personnel have access to the router. Also, consider implementing two-factor authentication (2FA) to enhance the security of your router.
6. Disable Telnet access
Telnet is an outdated and unencrypted protocol that transmits data in plain text form. Hackers may intercept and obtain login credentials using a sniffer. It is recommended to disable Telnet access to your Mikrotik router and use Secure Shell (SSH), which is a more secure protocol that uses encryption to protect data in transit.
7. Implement Access Control Lists (ACLs)
Access Control Lists (ACLs) allow you to control network traffic based on specified criteria. This gives you granular control over what traffic is allowed into and out of your network. Configure ACLs to permit only necessary traffic and deny all other traffic.
8. Use WPA2 for Wi-Fi security
Wi-Fi networks are susceptible to attacks such as eavesdropping, Man-In-The-Middle (MITM), and password cracking. To secure your Wi-Fi network, use Wi-Fi Protected Access 2 (WPA2) protocol. WPA2 uses Advanced Encryption Standard (AES) to encrypt traffic and is more secure than WEP and WPA.
9. Enable DHCP Snooping
DHCP Snooping is a security feature that prevents rogue DHCP servers from distributing IP addresses on your network. When enabled, it only allows DHCP servers that you have authorized to distribute IP addresses. This secures your network against DHCP spoofing attacks.
10. Implement Network Address Translation (NAT)
Network Address Translation (NAT) is a mechanism that hides private IP addresses used within an organization behind a single public IP address. NAT prevents direct access to devices on your network from the internet. This adds an extra layer of security to your network, reducing the risk of cyber attacks targeting your devices.
In conclusion, securing your Mikrotik router is a critical step towards safeguarding your network against cyber attacks. Following these steps will help you to harden the security of your router and minimize the risk of attacks. Remember to keep your router firmware up to date, configure firewall rules, and limit administrative access to the router. By implementing these measures, you can create a secure network environment and avoid becoming a victim to cyber attacks.


Post a Comment for "Configuring MikroTik Router Wireless Security Best Practices And Encryption"