Securing MikroTik RouterOS Tips For Hardening Your Network
We all know that security is an essential part of modern technology, and networks are no exception. The ever-increasing number of devices, applications, and users in today's networks can pose significant risks to the security of the network. That's why network hardening is crucial to maintaining the security of your network. Network hardening is the process of securing a network by reducing its vulnerability to attacks. This is achieved by removing all unnecessary services, protocols, and applications that could be exploited by an attacker. In this article, we'll discuss network hardening in detail and explore the different steps involved in the process. First and foremost, the objective of network hardening is to ensure that security is at the forefront of every decision made in regards to your network. For this to be achieved, several things must be taken into account. The first step in network hardening is conducting a comprehensive risk assessment to identify all possible risks and vulnerabilities in your network. This will help you determine what areas of your network require the most attention and effort when hardening. The next step is to develop a security plan that outlines all the necessary security measures that will be implemented. This plan should address all the identified risks and vulnerabilities and provide an action plan for mitigating each of them. After developing the security plan, the next step is to implement the necessary security measures. This includes ensuring that all software and firmware on your network are up to date and that all security patches have been applied. Additionally, all user accounts and passwords should be properly secured and regularly audited. Another crucial step in network hardening is configuring your network devices with the appropriate security settings. This includes configuring firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs) to protect your network. In addition to these measures, it is essential to monitor your network regularly and proactively identify any potential security threats. This can be achieved using network monitoring tools that scan the network for any unauthorized access points, unusual traffic patterns, or other anomalies. Finally, it's vital to educate your employees on the importance of network security and how they can help keep your network safe. This includes training them on how to identify potential security threats and how to report them to the appropriate personnel. In conclusion, network hardening is an essential process for maintaining the security of your network. By following the steps outlined in this article, you can significantly reduce the risk of a security breach and protect your network from potential threats. Remember to conduct a comprehensive risk assessment, develop a security plan, implement security measures, configure your network devices with appropriate settings, monitor your network regularly, and educate your employees. Stay safe, and keep your network secure! 



hardening network cyber defense vulnerabilities netbrain organizations helps requirements meet three breach their rules golden
mikrotik labs hardening routeros
hardening

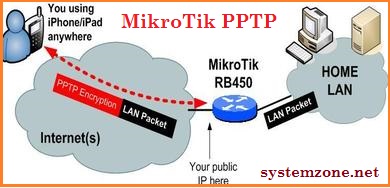

Post a Comment for "Securing MikroTik RouterOS Tips For Hardening Your Network"