Configuring MikroTik Router As A Transparent Proxy A Step-by-Step Tutorial
If you're wondering about the best way to use a proxy, it essentially comes down to two main methods; transparent and explicit. Each method has its own advantages and disadvantages, so it's crucial to choose the one that is best suited to your particular requirements.
Transparent Proxy
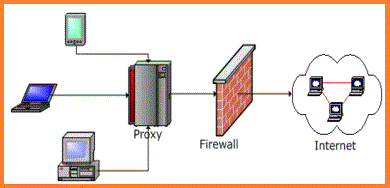
A transparent proxy is a server that sits between your computer and the Internet. It intercepts all requests made by your computer and forwards them on to the Internet. It's called a transparent proxy because it operates transparently to the end-user, meaning that the user does not need to configure anything on their computer to make use of it.
The main advantage of using a transparent proxy is that it requires no client-side setup. This makes it very easy to deploy and use. It also means that traffic can be filtered centrally, without the need for individual clients to be configured. This can be useful in situations where you want to apply filtering to your network, but do not want to configure each individual client. An example of this might be in a school or workplace environment.
Another benefit of using a transparent proxy is that it can perform caching of frequently accessed data. This can significantly reduce the amount of bandwidth required, improving the performance of your network.
Explicit Proxy
An explicit proxy, on the other hand, requires the user to configure their computer to use the proxy. This means that the user must enter the IP address and port number of the proxy server into their web browser or operating system. This can be done manually or via a script or group policy.
The advantage of using an explicit proxy is that it offers greater control and flexibility than a transparent proxy. It allows you to apply filtering and policies based on individual clients or groups of clients. This can be useful in situations where you need to apply different policies to different users or departments. It also allows you to log traffic at a more detailed level.
One disadvantage of using an explicit proxy is that it requires client-side configuration. This can be more challenging to deploy in larger environments or where there are a large number of clients. It also makes it harder to enforce policies, as users can bypass the proxy if they wish.
Which Method Should I Use?
So, which method should you use? There is no one-size-fits-all answer to this question, as it depends on your particular requirements. Here are some factors to consider when making your decision:
Deployment Ease
As we mentioned earlier, a transparent proxy is much easier to deploy than an explicit proxy. If you have a large number of clients or do not want to configure each individual client, then a transparent proxy may be the best option for you.
Flexibility
An explicit proxy offers greater flexibility and control than a transparent proxy. If you have specific policies that you need to apply to individual clients or groups of clients, then an explicit proxy may be the best option for you.
Security
A transparent proxy can be easier to bypass than an explicit proxy. If security is a concern, then an explicit proxy may be a better option. You can enforce policies and log traffic at a more detailed level, which can help you to identify any security breaches.
Bandwidth
A transparent proxy can help to reduce bandwidth usage by caching frequently accessed data. If you have a limited bandwidth connection, then a transparent proxy may be the best option for you.
Summary
As you can see, both transparent and explicit proxies have their own advantages and disadvantages. Your choice will depend on your specific requirements.
If you need ease of deployment and performance, then a transparent proxy may be the best option. If you need greater control and security, then an explicit proxy may be the best option. Ultimately, the choice is yours.
We hope this article has helped you to understand the difference between transparent and explicit proxies. Remember to choose the method that is best suited to your needs.


Post a Comment for "Configuring MikroTik Router As A Transparent Proxy A Step-by-Step Tutorial"