SSL Interception And Content Inspection MikroTik Router Proxy Explained
Let's talk about a valuable tool for web developers: Interception Proxy. This tool provides a way to inspect web traffic, allowing developers to debug problems and improve their applications. One of the challenges developers face is encrypting their web traffic, which can lead to issues with inspecting traffic. Fortunately, Let's Encrypt provides a solution to this problem.
Let's Encrypt
Let's Encrypt is a certificate authority that provides free SSL/TLS certificates. It makes it easy for websites to switch from HTTP to HTTPS, which provides a more secure connection between the user and the website. However, HTTPS can complicate debugging and testing, as encrypted traffic is difficult to inspect.
Interception Proxy
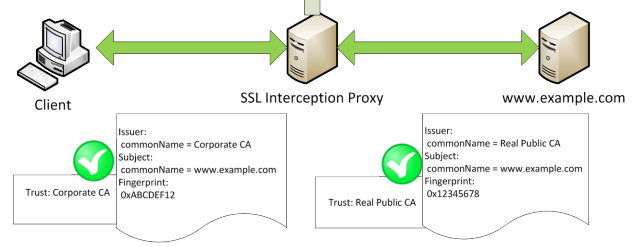
Interception Proxy is a tool that allows developers to inspect web traffic. It can be used to identify and fix issues with website functionality, improve performance, and debug problems. However, if a website is using HTTPS, inspection becomes more difficult.
Let's Encrypt provides a solution to this problem by allowing developers to generate their own SSL/TLS certificates. By including a Let's Encrypt certificate in the interception proxy, developers can then decrypt the HTTPS traffic, allowing them to inspect it as they would unencrypted traffic.
How to Set Up Let's Encrypt with Interception Proxy
Setting up Let's Encrypt with interception proxy is a relatively straightforward process. There are several steps that need to be followed to ensure that the interception proxy is properly configured.
Step 1: Install Certbot
The first step is to install Certbot, which is a tool that allows you to generate Let's Encrypt certificates. Certbot is available for most Linux distributions and can be installed using the package manager.
Step 2: Generate Let's Encrypt Certificates
Once Certbot is installed, you can generate a Let's Encrypt certificate for the domain that you want to inspect. This can be done by running the following command:
sudo certbot certonly --standalone -d example.com This will generate a Let's Encrypt certificate for the domain example.com and save it on your server.
Step 3: Configure the Interception Proxy
Next, you will need to configure the interception proxy to use the Let's Encrypt certificate. This can be done by adding the certificate to the interception proxy's configuration file.
In the configuration file, you will need to specify the location of the Let's Encrypt certificate and the private key that was generated when the certificate was created. You will also need to configure the interception proxy to use the certificate and key for HTTPS traffic.
Step 4: Start the Interception Proxy
Once the configuration file has been updated, you can start the interception proxy. The proxy will now be able to intercept HTTPS traffic and decrypt it using the Let's Encrypt certificate.
Conclusion
Interception Proxy is a powerful tool for web developers, allowing them to inspect web traffic and debug problems with their applications. However, when working with HTTPS traffic, inspection becomes more difficult. Let's Encrypt provides a solution to this problem by allowing developers to generate their own SSL/TLS certificates and include them in the interception proxy's configuration.
If you are a web developer, I highly recommend taking the time to set up Let's Encrypt with interception proxy. It will make your job much easier and allow you to deliver better, more secure applications.
Thank you for taking the time to read this article. I hope you found it informative and helpful. If you have any questions or comments, please do not hesitate to leave them below.



Post a Comment for "SSL Interception And Content Inspection MikroTik Router Proxy Explained"