Securing Remote Access With MikroTik Router VPN Best Practices And Encryption
If you're one of the millions of people who are working remotely, you know how important it is to have a secure connection to your office network. Whether you're accessing sensitive information or just trying to get your work done, you need to be sure that your connection is safe from prying eyes and hackers. Luckily, there are a number of secure remote access solutions available that can help you stay connected and protected. Here are five key considerations that you should keep in mind as you evaluate your options.
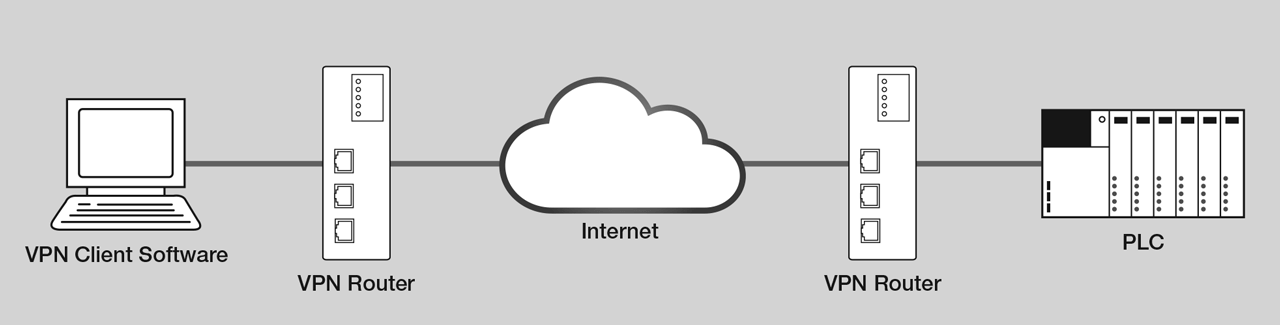
1. Encryption
The first and most important consideration when it comes to secure remote access is encryption. Encryption is the process of encoding data so that it can't be read by anyone who doesn't have the right key. This ensures that any information you send over the internet is secure and private. Look for remote access solutions that use strong encryption standards like AES-256.
2. Authentication
Authentication is the process of verifying the identity of a user. This is important because it prevents unauthorized access to your network. When evaluating remote access solutions, look for options that require multi-factor authentication, which means that users must provide more than one form of verification to access the network. This could include a password, a fingerprint, or a smart card.
3. Access Controls
The next thing to consider is access controls. Access controls are the rules that determine which users are allowed to access which resources on your network. Look for remote access solutions that allow you to set up role-based access controls. This means that you can define different levels of access for different users, which can help prevent unauthorized access to sensitive data.
4. Logging and Auditing
Logging and auditing are important for keeping track of who is accessing your network and what they're doing while they're there. Make sure that the remote access solution you choose has robust logging and auditing capabilities. This will allow you to track user activity and detect any suspicious behavior.
5. User Experience
The final consideration is user experience. A good remote access solution should be easy to use and should integrate seamlessly with the tools you use every day. Look for options that offer a user-friendly interface and that allow users to access network resources quickly and easily.
By keeping these five key considerations in mind, you can choose a remote access solution that will keep you and your network secure while also providing a seamless user experience. Remember to prioritize encryption, authentication, access controls, logging and auditing, and user experience as you evaluate your options, and you'll be well on your way to a more secure remote working experience.



Post a Comment for "Securing Remote Access With MikroTik Router VPN Best Practices And Encryption"