Boosting Network Speed With MikroTik RouterOS
A critical vulnerability has been discovered in MikroTik RouterOS that allows attackers to launch DOS attacks using multiple vectors. The exploit can be used to crash the router and can ultimately leave the network vulnerable to further attacks.

The Details:
The vulnerability has been identified in MikroTik RouterOS versions 6.45.1 and below. While the exploit is passive in nature, it can be used to perform a wide range of attacks, including DNS amplification attacks, SYN flood attacks, and HTTP flood attacks.
What is a DOS Attack?
A DOS (Denial of Service) attack is a type of attack that attempts to overload a server or network by flooding it with traffic. The purpose of a DOS attack is to make the server or network unavailable to legitimate users. DOS attacks are relatively easy to perform, and can often be launched from a single computer.
How Does the MikroTik RouterOS Exploit Work?
The MikroTik RouterOS exploit works by using a passive exploit to crash the router. The exploit is passive in nature, meaning that it does not actively attempt to exploit vulnerabilities in the router's software. Instead, it relies on a specific configuration of the router to create conditions that can be exploited by an attacker.
How Can the MikroTik RouterOS Exploit Be Used?
The MikroTik RouterOS exploit can be used to perform a wide range of DOS attacks, including DNS amplification attacks, SYN flood attacks, and HTTP flood attacks. These attacks can be used to overload the router and take it offline, leaving the network vulnerable to further attacks.
DNS Amplification Attacks:
DNS amplification attacks involve flooding a DNS server with requests that require a large amount of data to be transmitted in response. The attacker sends requests to the DNS server with a spoofed IP address that appears to come from the target of the attack. The DNS server responds with a large amount of data, which is sent to the target system, overwhelming it and causing it to crash.
SYN Flood Attacks:
SYN flood attacks involve flooding a target system with a large number of SYN packets. SYN packets are used to initiate a connection with another computer. When the target system receives a SYN packet, it responds with a SYN + ACK packet. This creates an unacknowledged connection which eventually overwhelms the system's resources, causing it to crash.
HTTP Flood Attacks:
HTTP flood attacks involve flooding a web server with HTTP requests. The attacker uses a large number of computers to simultaneously send requests to the server, overloading it with traffic and causing it to crash.
How Can the MikroTik RouterOS Exploit Be Mitigated?
The MikroTik RouterOS exploit can be mitigated by upgrading to version 6.45.2 or later. Additionally, the following steps can be taken to reduce the risk of a DOS attack:
- Configure firewalls to block traffic from known malicious IP addresses.
- Use intrusion prevention software to monitor the network for suspicious activity.
- Reduce the attack surface by disabling unnecessary services and closing unused ports.
- Implement strong passwords and two-factor authentication to prevent unauthorized access to the network.
It is important to note that while these steps can help to reduce the risk of a DOS attack, they cannot guarantee protection against all attacks. It is essential to stay vigilant and monitor the network for signs of suspicious activity.
Conclusion:
The MikroTik RouterOS vulnerability is a serious threat to network security, as it can be used to launch a wide range of DOS attacks. It is important for network administrators to take steps to mitigate the risk of an attack, and to monitor the network for suspicious activity. Upgrading to the latest version of RouterOS is essential to protect against this vulnerability and ensure the security of the network.
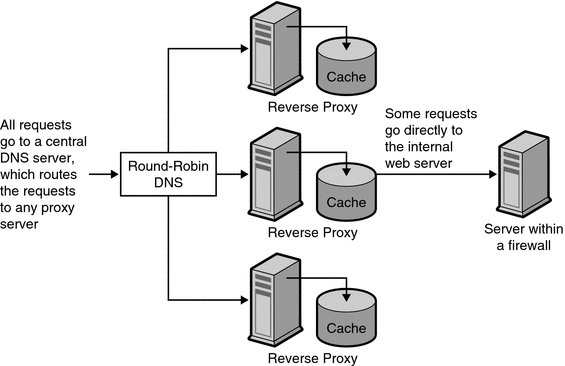
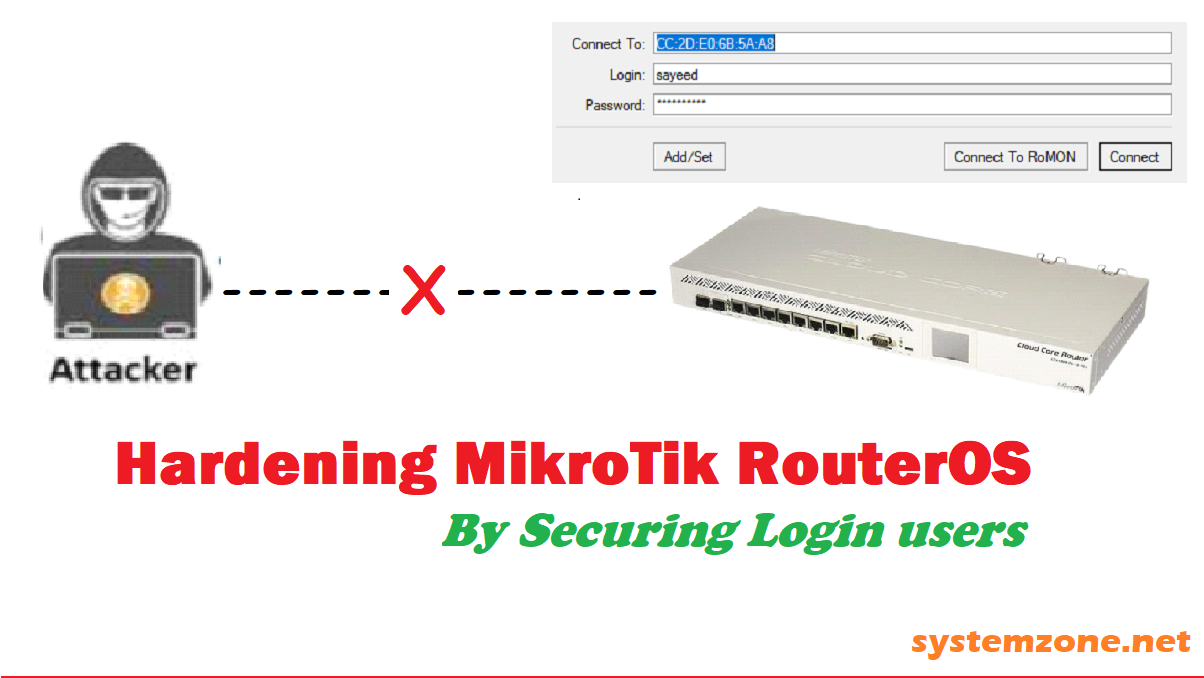


Post a Comment for "Boosting Network Speed With MikroTik RouterOS"