Exploring MikroTik Proxy Server SSL Interception And Inspection
As we traverse the internet, we're left exposed to a world of hackers, spammers, and other threats that can compromise our sensitive information. To prevent this, a technique called SSL Inspection has evolved in recent times, wherein HTTPS traffic is decrypted to be inspected for potential threats. In this blog post, we'll take a deeper dive into SSL Inspection, how it works, and whether it's worth it or not.
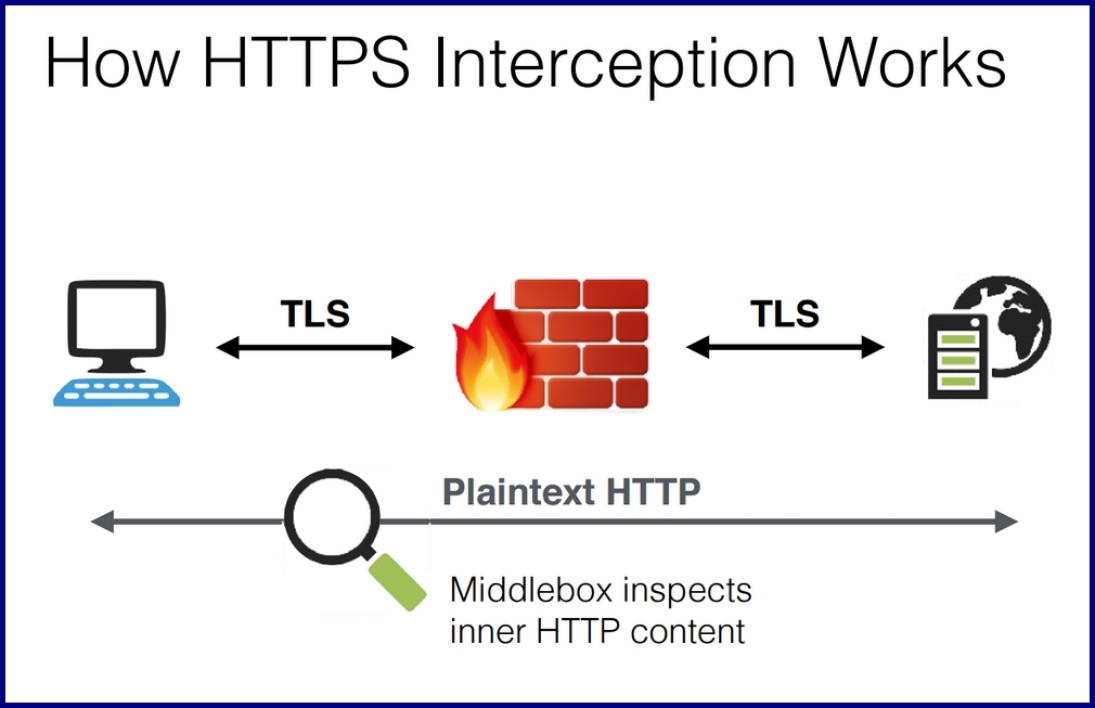
So, what exactly is SSL Inspection? Essentially, SSL Inspection, also known as HTTPS Interception or SSL Decryption, is a process through which encrypted traffic flowing between the web server and browser is decrypted, inspected for threats, and then re-encrypted before delivery to the end-user.
Now that we understand what SSL Inspection is, let's delve into how it works in detail:
How SSL Inspection Works
SSL Inspection can be divided into several steps:
Step 1: Intercepting HTTPS Traffic
The first step in the SSL Inspection process is to intercept the HTTPS traffic, which is encrypted using SSL/TLS certificates. To do this, we must have a trusted root certificate on our system, which will generate a certificate for each website we visit. This certificate would then be used for HTTPS communication between our browser and the website.
Step 2: Decrypting Traffic
Once the HTTPS traffic is intercepted, it must be decrypted to be inspected. This is done using the generated certificate, which acts as a 'man-in-the-middle'. It decrypts the SSL/TLS traffic and re-encrypts it using a certificate that's signed by a trusted Certificate Authority.
Step 3: Inspection
Now that the HTTPS traffic has been decrypted and re-encrypted using a trusted certificate, it can be inspected for threats, such as malware, viruses, or unwanted content. This inspection can be performed at various levels, including application level, content level, and context level, depending on the type of inspection being performed.
Step 4: Re-encrypting and Delivery
The final step in the SSL Inspection process is to re-encrypt the traffic using the original certificate issued by the website and deliver it to the end-user.
Now that we understand how SSL Inspection works, let's examine whether it's worth the effort:
Is SSL Inspection Worth It?
There are pros and cons to SSL Inspection, depending on how it's perceived by the end-user and how it's implemented:
Pros:
- Increased Security: SSL Inspection can significantly improve security by detecting and preventing threats that may go undetected in encrypted traffic.
- Compliance: It can help organizations meet compliance requirements by ensuring that all web traffic is inspected for potential threats.
- Improved Productivity: By blocking access to non-work-related sites and activities that could lead to security breaches, organizations can improve productivity.
Cons:
- Potential Privacy Concerns: Many end-users perceive SSL Inspection as invasive and a violation of privacy as it intercepts encrypted traffic.
- Increased Complexity: Implementing SSL Inspection requires significant resources, including hardware and software, as well as specialized knowledge to configure and maintain.
- Detection Limitations: SSL Inspection may not detect some malware and threats, such as those that use TLS 1.3 or newer encryption standards.
Despite the pros and cons, SSL Inspection can be a valuable tool in promoting security protocols and detecting potential threats to an organization's sensitive information. However, it's important to consider the privacy implications and resource requirements that come with implementing SSL Inspection.
Conclusion:
In conclusion, SSL Inspection is an essential tool in our fight against internet threats. It provides a level of protection that would otherwise be impossible with encrypted traffic. However, it's also important to consider the potential downsides and the resources required to implement it effectively.
Thanks for reading this post on SSL Inspection. We hope it was informative and helped you understand this critical security technique a bit better.



Post a Comment for "Exploring MikroTik Proxy Server SSL Interception And Inspection"