Advanced MikroTik Router Firewall Rules For VPN Security
If you want to maintain optimal security of your network, then you need to use a reliable tool that will help you in this regard. Among the various options available, MikroTik L2TP/IPsec VPN Firewall Rules is a great choice, as it offers a robust and comprehensive approach to protecting your network.
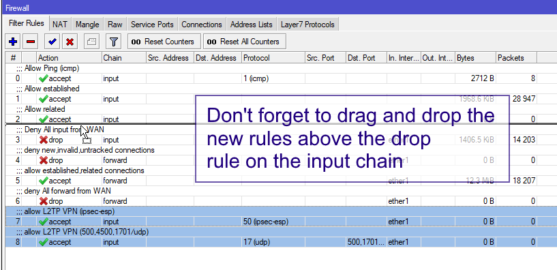
What is MikroTik L2TP/IPsec VPN Firewall Rules?
MikroTik is a well-known brand in the field of network security, renowned for producing reliable, powerful, and user-friendly tools that assist individuals and organizations in securing their networks. One such tool from MikroTik is the L2TP/IPsec VPN Firewall Rules.
How does it work?
A VPN (Virtual Private Network) is a secure and encrypted connection between a user and a remote server that allows the user to access a network securely. It is a great tool for maintaining privacy and protecting your sensitive data, such as login credentials, bank account numbers, and more, from potential intruders.
The L2TP (Layer 2 Tunneling Protocol) is a protocol that creates a VPN connection between two endpoints. IPsec (Internet Protocol Security) is a protocol that secures data transmission over the internet. This powerful and secure combination ensures a robust VPN connection that is safe from prying eyes.
What are the benefits of MikroTik L2TP/IPsec VPN Firewall Rules?
1. Secure Data Transmission - MikroTik L2TP/IPsec VPN Firewall Rules provide secure data transmission over the internet, ensuring that your sensitive data is safe and protected from potential intruders.
2. Easy Configuration - The tool offers an intuitive graphical user interface that makes it easy to configure and use. Users can quickly create and customize their VPN connections with ease, even without prior technical knowledge.
3. Multi-Platform Compatibility - MikroTik L2TP/IPsec VPN Firewall Rules are compatible with various platforms, including Windows, macOS, iOS, Android, and Linux. This ensures that users can use the tool from any device without worry.
4. Firewall Rules - The MikroTik L2TP/IPsec VPN Firewall Rules feature also includes a set of firewall rules to further enhance security. These rules ensure that only authorized traffic enters the network, protecting against potential threats such as DDoS attacks, malware infections, and more.
How can you use MikroTik L2TP/IPsec VPN Firewall Rules?
To use MikroTik L2TP/IPsec VPN Firewall Rules, you need to follow the following steps:
1. Install and Configure MikroTik Firewall - Install the MikroTik Firewall and configure it to your liking. You can customize the rules to ensure optimal security, based on your network's specific needs.
2. Create a VPN Connection - Once you've configured the firewall, it is time to create a VPN connection. To do this, go to the VPN menu and click L2TP Server. From there, configure the necessary settings as appropriate, such as username, password, and IP range.
3. Configure Firewall Rules - After creating the VPN connection, it is time to configure the Firewall rules. Go to the Firewall menu and click on the NAT tab. From there, click on the + sign to create a new rule. Configure it according to your specific needs, ensuring that you set the appropriate sources and destinations.
Conclusion
The MikroTik L2TP/IPsec VPN Firewall Rules is a powerful and comprehensive tool that offers robust security measures to ensure optimal network safety. With its intuitive user interface, ease of configuration, and multi-platform compatibility, it's an ideal choice for individuals and organizations looking to secure their networks. Its firewall rules provide additional layers of security, further helping to keep sensitive network data safe from potential threats.
Overall, I highly recommend MikroTik L2TP/IPsec VPN Firewall Rules as a highly effective, reliable solution for securing your network.



Post a Comment for "Advanced MikroTik Router Firewall Rules For VPN Security"