VPN Protocols Compared Choosing The Best Option For Your Needs
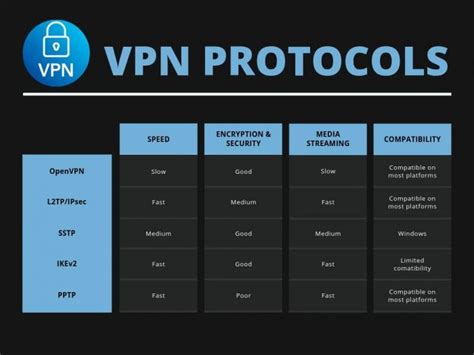
When it comes to online security and privacy, one of the most useful tools in your arsenal is a Virtual Private Network (VPN). But not all VPNs are created equal. One of the key factors that determine the quality and security of a VPN is the protocol it uses. In this article, we’ll take a closer look at VPN protocols, including what they are, how they work, and which ones you should use to maximize your online safety. We’ll cover everything you need to know in a simple, easy-to-understand format, so you can make informed decisions about your online security. What are VPN protocols? VPNs work by encrypting your internet traffic and rerouting it through a private server, creating a secure and private connection between your device and the internet. But how exactly does this work? VPN protocols are the set of rules and procedures that govern how the VPN creates and maintains this secure connection. Think of it like a secret handshake that allows your device and the VPN server to communicate securely and exchange information without anyone else being able to spy on or intercept it. There are many different types of VPN protocols out there, each with its own strengths and weaknesses. Some are faster, some are more secure, and some work better on certain types of networks or devices. Here are some of the most common VPN protocols you’re likely to encounter: 1. PPTP (Point-to-Point Tunneling Protocol) PPTP is one of the oldest VPN protocols around, and one of the easiest to set up. It’s also one of the weakest in terms of security, as it uses relatively weak encryption and has vulnerabilities that can be exploited by hackers. While PPTP isn’t recommended for use in high-security situations, it can be a good choice for basic online browsing and streaming. 2. L2TP/IPSec (Layer 2 Tunneling Protocol with Internet Protocol Security) L2TP/IPSec is a combination of two different VPN protocols, and it’s one of the most commonly used protocols for commercial VPN services. It’s more secure than PPTP, as it uses stronger encryption and tunnelling protocols. L2TP is often used in combination with IPSec, which provides an extra layer of security by encrypting the data as it travels between the VPN server and your device. L2TP/IPSec is a good all-around choice for most users who want a balance between speed and security. 3. SSTP (Secure Socket Tunneling Protocol) SSTP is a VPN protocol that was developed by Microsoft, and it’s designed to be especially secure and resistant to hacking and other attacks. It uses SSL/TLS encryption, the same encryption used by HTTPS websites, to create a secure tunnel between your device and the VPN server. SSTP is a good choice for users who want maximum security and privacy, but it can be slower than some other protocols due to the high level of encryption. 4. OpenVPN OpenVPN is an open-source VPN protocol that’s widely regarded as one of the most secure and flexible protocols available. It uses OpenSSL encryption to create a secure connection between your device and the VPN server, and it’s highly configurable and customizable. OpenVPN can be used on a wide variety of devices and operating systems, and it supports multiple encryption protocols, making it a versatile choice for users who want the highest level of security and flexibility. 5. IKEv2 (Internet Key Exchange Version 2) IKEv2 is a VPN protocol that was developed by Microsoft and Cisco, and it’s designed to be fast, reliable, and secure. It’s particularly well-suited for use on mobile devices and networks, as it’s able to quickly and seamlessly switch between different types of networks and maintain a stable connection. IKEv2 uses strong encryption and tunnelling protocols to create a secure connection between your device and the VPN server, and it’s a good choice for users who want a high-speed, reliable VPN that works well on mobile devices. Which VPN protocol should I use? So, with all these different VPN protocols to choose from, how do you know which one to use? The truth is, there’s no one-size-fits-all answer to this question. The best VPN protocol for you will depend on a variety of factors, including your specific needs and preferences, your device and operating system, and the networks you’ll be using your VPN on. Here are some general guidelines to help you choose the best VPN protocol for your needs: - If you want maximum security and don’t mind sacrificing some speed, then SSTP or OpenVPN are good choices. - If you want a good balance between speed and security, then L2TP/IPSec is a good all-around choice. - If you’re using a mobile device or frequently switching between networks, then IKEv2 is probably your best option. - If you’re just doing basic online browsing or streaming and don’t need the highest level of security, then PPTP can be a good choice. It’s also worth noting that some VPN providers will automatically select the best protocol for your needs based on your device and network, so you don’t need to worry too much about which protocol to use. Conclusion VPN protocols are an important factor to consider when choosing a VPN provider, as they determine the level of security and privacy you can expect from your VPN connection. By understanding the different types of VPN protocols and their strengths and weaknesses, you can make informed decisions about the best VPN for your needs. Remember to consider factors like your device, operating system, and the networks you’ll be using your VPN on when choosing a protocol, and always make sure to choose a reputable VPN provider that offers robust security features and excellent customer support. With the right VPN protocol and provider, you can enjoy a safe, secure, and private online experience. 


vpn protocols usenet
vpn protocols
vpn protocols fungerer hvordan protokoll techicy hva protokoller hvad
protocols vpn websta techuseful



Post a Comment for "VPN Protocols Compared Choosing The Best Option For Your Needs"