Understanding Proxy Server Authentication Methods
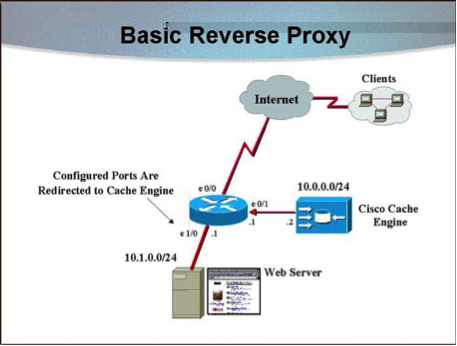
When you go online, you are using a proxy server, although most people are not even aware of it. Proxy servers are a crucial part of the internet infrastructure. They are used by internet service providers, businesses, and private individuals alike. In this post, we will delve into the topic of proxy servers and explain why they are so important. Firstly, what exactly is a proxy server? To put it simply, a proxy server is a server that acts as a middleman between your device and the internet. When you make a request to access a website, your device sends the request to the proxy server, and the proxy server then forwards the request to the website. The website sends the response back to the proxy server, and the proxy server then sends the response to your device. You may be wondering why a middleman is necessary. There are several reasons why a proxy server is used. One of the key reasons is for security purposes. Proxy servers can help protect your device and your data from malicious actors online. By acting as a barrier between your device and the internet, proxy servers can block malicious websites and prevent hackers from accessing your data. Another reason why proxy servers are used is for privacy. Proxy servers can help protect your privacy by hiding your IP address. When you use a proxy server, the website you are accessing only sees the IP address of the proxy server, not your device's IP address. This means that your online activity is more difficult to track, which can be crucial for businesses and individuals that value privacy. Proxy servers also have practical uses for businesses and organizations. For example, proxy servers can be used to control access to certain websites or online services. This can be important for businesses that need to restrict access to certain websites for security reasons. Proxy servers can also be used to speed up web browsing by caching frequently accessed websites. There are several different types of proxy servers. The most common types are HTTP proxies and SOCKS proxies. HTTP proxies are used for web browsing, while SOCKS proxies can be used for a wider range of online services. Another type of proxy server is a reverse proxy. Reverse proxies are used to protect web servers from attacks by acting as a barrier between the internet and the web server. There are also different levels of anonymity when using a proxy server. Transparent proxies do not hide your IP address and are mainly used for caching purposes. Anonymous proxies hide your IP address but can still be traced back to the originating device. Elite proxies are the most anonymous and do not reveal any information about the originating device. While there are many benefits to using a proxy server, there are also some drawbacks. One of the main drawbacks is that using a proxy server can slow down web browsing. This is because each request has to go through the proxy server before reaching the website. Another drawback is that not all websites are compatible with proxy servers. Some websites may block access from proxy servers for security reasons. In conclusion, proxy servers are an important part of the internet infrastructure. They provide security and privacy benefits and have practical uses for businesses and organizations. However, there are also some drawbacks to using proxy servers, such as slower web browsing and compatibility issues. Overall, proxy servers are a crucial tool for anyone that uses the internet regularly. Whether you are a business owner or just a regular user, using a proxy server can help protect your online activity and keep you safe from malicious actors online. 



proxy authentication web windows
proxy server authentication ldap
proxy understanding servers



Post a Comment for "Understanding Proxy Server Authentication Methods"