Securing Web Traffic With MikroTik Router SSL Certificates
A MikroTik router is a popular choice among farmers who need a reliable and secure network. However, it's important to take extra measures to ensure that the network stays secure from unwanted visitors. One such measure is implementing port knocking, which we'll discuss in detail below.
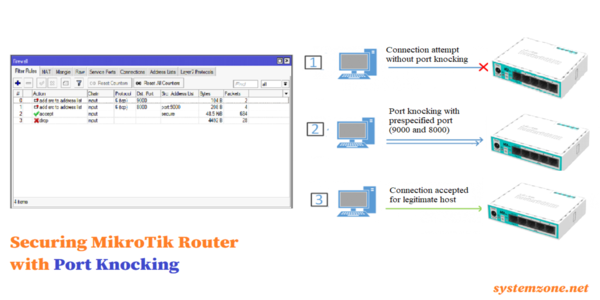
What is Port Knocking?
Port knocking is a security technique used to protect a network from unauthorized access. It works by monitoring network traffic and looking for specific "knock" sequences. These knock sequences are a series of connection attempts made to specific ports in a specific order. Once the correct sequence is detected, the network opens up a previously blocked port or service, allowing authorized users to access the network.
How Does Port Knocking Work?
To understand how port knocking works, let's walk through an example scenario:
A farmer wants to access his MikroTik router from outside his network. First, he must send a connection attempt (knock) to three specific ports in a specific order. Let's say the ports are 1000, 2000, and 3000. Once the router detects the correct sequence, it will open up port 22 (which is typically used for SSH) for a set amount of time, allowing the farmer to access the router. If the farmer fails to send the correct sequence in the correct order, the router remains inaccessible.
Why is Port Knocking Important for Farmers Who Use MikroTik Routers?
Port knocking is important for farmers who use MikroTik routers because it adds an extra layer of security to the network. By implementing port knocking, farmers can significantly reduce the risk of unauthorized access to their network, which can lead to data breaches, theft of personal information, and other security threats.
How to Implement Port Knocking on a MikroTik Router
Implementing port knocking on a MikroTik router is a multi-step process. We've outlined the key steps below:
Step 1: Configure Firewall Rules
The first step in implementing port knocking on a MikroTik router is to configure firewall rules. We'll create three firewall rules to handle the incoming connection attempts (knocks) and to open up the desired service (SSH).
Open up the Winbox utility and connect to your MikroTik router. Then, navigate to the "IP" tab and click on "Firewall". Click on the "Filter Rules" tab and create the following three rules:
- Rule 1: Block all incoming traffic to the desired service (SSH)
- Action: Drop
- Chain: Input
- Protocol: TCP
- Dst. Port: 22
- Comment: "Block SSH until knock sequence is detected"
- Rule 2: Allow incoming traffic to the knock ports (1000, 2000, 3000)
- Action: Accept
- Chain: Input
- Protocol: TCP
- Dst. Port: 1000-3000
- Comment: "Allow incoming traffic to knock ports"
- Rule 3: Log incoming knock sequences and open the desired service (SSH)
- Action: Accept
- Chain: Input
- Protocol: TCP
- Src. Address List: Dynamic Port Knocker
- Src. Port: Any
- Dst. Port: 22
- Comment: "Log knock sequence and open SSH for authorized users"
Once you've created these rules, click "Apply" to save them.
Step 2: Create a Port Knocker Script
The next step is to create a Port Knocker script that will send the correct sequence of connection attempts (knocks) to the MikroTik router. You can use an existing Port Knocker script or create your own. Here's an example Port Knocker script:
#!/bin/bash # Get the IP address of the MikroTik router ROUTER_IP="192.168.1.1" # Set up the knock sequence (ports and delay) KNOCK_SEQUENCE="1000 2000 3000" DELAY="1" # Send the knock sequence to the MikroTik router for PORT in $KNOCK_SEQUENCE; do (sleep "$DELAY"; echo <"<$PORT"; sleep "$DELAY") | telnet "$ROUTER_IP" >/dev/null 2>&1 doneSave this script as "portknocker.sh" and make it executable using the following command:
chmod +x portknocker.shStep 3: Configure the Port Knocker Script
The next step is to configure the Port Knocker script with your MikroTik router's IP address and the knock sequence you configured in Step 1. Open up the "portknocker.sh" script in a text editor and modify the following lines:
ROUTER_IP="192.168.1.1" KNOCK_SEQUENCE="1000 2000 3000"Replace "192.168.1.1" with your MikroTik router's IP address and replace "1000 2000 3000" with the knock sequence you configured in Step 1.
Step 4: Test the Port Knocking Implementation
The final step is to test the port knocking implementation. First, make sure the "portknocker.sh" script is executable by running this command:
chmod +x portknocker.shThen, run the script by executing this command:
./portknocker.shIf the knock sequence is correct, the MikroTik router's firewall will log the connection attempts and open up the SSH service for a set amount of time.
Conclusion
Port knocking is a powerful security technique that can help farmers keep their MikroTik router networks secure. By following the steps outlined in this article, farmers can implement port knocking and significantly reduce the risk of unauthorized access to their network.
Implementing port knocking may seem daunting at first, but the extra security it provides is well worth the effort. We hope this article has been helpful in explaining how to implement port knocking on a MikroTik router. Happy farming!




Post a Comment for "Securing Web Traffic With MikroTik Router SSL Certificates"