MikroTik RouterOS VPN Multi-Factor Authentication And Certificate Management
Are you a Mikrotik user who has recently updated your RouterOS? If so, you may have noticed some changes when it comes to configuring your IPSEC L2TP VPN. Our team at Chef People has been investigating these changes and we’re here to share what we’ve found so far.
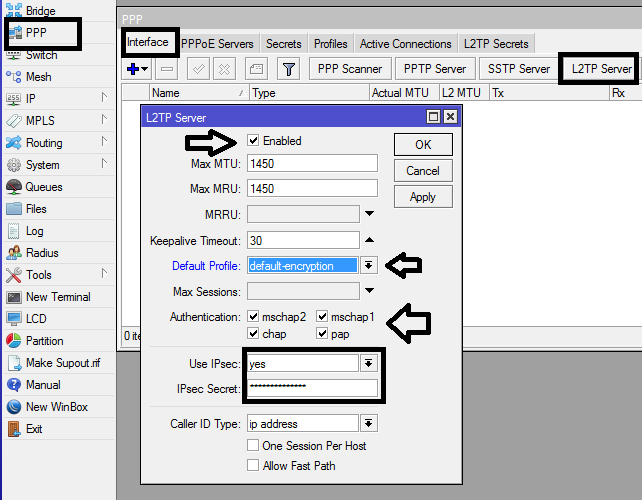
The Changes
With the latest update, there are a few notable changes to the process for configuring your IPSEC L2TP VPN:
- The IPSEC policy for L2TP is now created automatically when the L2TP server is enabled.
- The default IPSEC proposal that is used has been changed from aes-128-cbc to aes-256-cbc.
- The secret used for the L2TP clients is now stored encrypted in the configuration.
What This Means for You
If you’ve been using Mikrotik’s IPSEC L2TP VPN in the past, you may need to make some changes to ensure that your configuration is up-to-date:
Verify Your IPSEC Policy
With the latest update, the IPSEC policy for L2TP is created automatically when you enable the L2TP server. However, it’s still important to verify that the policy is correct. You can do this by navigating to IP > IPsec > Policies and ensuring that the policy has the following settings:
- Protocol: All
- Src. Address: 0.0.0.0/0
- Dst. Address: 0.0.0.0/0
- Action: Encrypt
- Level: unique
- Proposal: aes-256-cbc
Update Your Clients’ Secrets
The latest update now stores the secrets used for L2TP clients encrypted in the configuration. This means that if you had secrets set up previously, they will need to be updated. You can do this by navigating to PPP > Secrets and editing the appropriate secret.
Check Your NAT and Firewall Rules
Finally, it’s important to check your NAT and Firewall rules to ensure that they are configured correctly for L2TP VPN traffic. You’ll need to allow incoming UDP traffic on port 1701 and ensure that the VPN subnet is NATed to your public IP address.
Conclusion
While the changes to Mikrotik’s IPSEC L2TP VPN configuration process may seem daunting at first, they are relatively straightforward once you know what to look for. By following the steps outlined above, you can ensure that your VPN configuration is up-to-date and secure.
Stay tuned for more updates from Chef People as we continue to explore changes in the tech world that impact businesses like yours.


Post a Comment for "MikroTik RouterOS VPN Multi-Factor Authentication And Certificate Management"