Transparent Proxy Authentication With MikroTik RouterOS
Have you ever wondered how your internet service provider (ISP) manages to filter your internet traffic and keep you safe from potential threats? Or, have you ever experienced slow internet speeds and wondered if there's a way to optimize your internet connection? In this age of internet dependency, it's important to understand how internet traffic is managed and optimized. In this post, we'll discuss the difference between transparent and explicit proxies and which method you should use.

What Is a Proxy?
Before we get into the difference between transparent and explicit proxies, it's important to understand what a proxy is and how it works. In simple terms, a proxy is an intermediary server that sits between your computer or device and the internet. When you request a website or resource on the internet, your computer sends a request to the proxy server instead of directly to the website or resource. The proxy server then retrieves the website or resource on your behalf and sends it back to your computer.
A proxy server can be used for several purposes, including:
- Filtering and monitoring internet traffic
- Caching frequently accessed content to reduce bandwidth usage and improve website load times
- Bypassing internet restrictions and censorship
Transparent Proxy
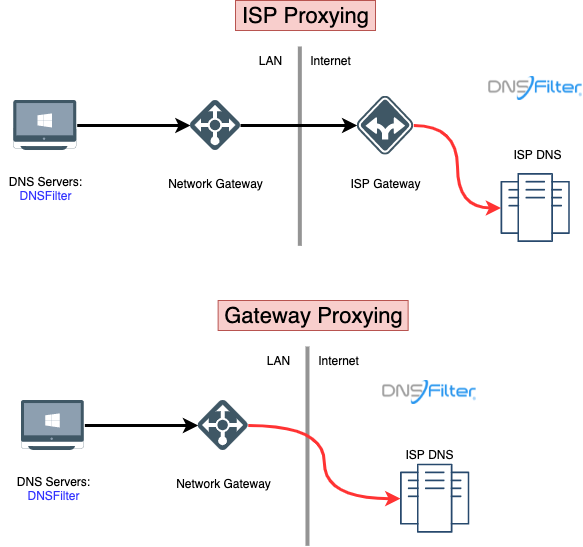
A transparent proxy, also known as an inline or intercepting proxy, is a proxy server that sits between your computer and the internet without requiring any configuration or settings on your end. This means that the transparent proxy is automatically configured to intercept and forward internet traffic without your knowledge or consent.
The use of transparent proxies is common in corporate and educational environments to monitor and regulate internet usage. Transparent proxies work by intercepting and analyzing internet traffic, blocking or allowing certain content or websites based on predefined policies, and logging user activity.
Explicit Proxy
An explicit proxy requires you to configure your computer or device to use a proxy server by specifying the proxy server's IP address and port number in your device's network settings or through a web proxy auto-discovery (WPAD) file. Unlike a transparent proxy, explicit proxies give you control over which traffic is sent through the proxy server and which traffic is sent directly to the internet.
Explicit proxies are commonly used in corporate environments to optimize internet traffic, reduce bandwidth usage, and improve website load times. Explicit proxies work by caching frequently accessed content, compressing web content to reduce the amount of data sent over the network, and filtering out unwanted traffic and content.
Which Method Should You Use?
So, now that we've discussed the difference between transparent and explicit proxies, which method should you use? The answer depends on your specific needs and requirements.
Transparent proxies are ideal for corporate and educational environments that require strict internet usage policies and monitoring. With a transparent proxy, you can easily filter and block unwanted content and keep track of user activity without requiring any configuration or settings from the end-user.
On the other hand, explicit proxies are ideal for optimizing internet traffic and improving website load times. By configuring your computer or device to use an explicit proxy, you can reduce bandwidth usage and improve website load times by caching frequently accessed content and compressing web content.
Conclusion
In conclusion, understanding the difference between transparent and explicit proxies is crucial in optimizing your internet connection and keeping yourself safe on the internet. While transparent proxies are ideal for corporate and educational environments that require strict internet usage policies and monitoring, explicit proxies are ideal for optimizing internet traffic and improving website load times.
Whether you choose to use a transparent or explicit proxy, it's important to understand how they work and how they can affect your internet experience. By staying informed and educated, you can make the best choice for your specific needs and requirements.

Post a Comment for "Transparent Proxy Authentication With MikroTik RouterOS"